A Year After Lockdown: Stalkerware on the Rise


Is someone in your household spying on you?
Increasingly, the answer could be yes, according to research from Norton Labs.
More people have begun using technology to spy on others — including significant others — since the beginning of the global pandemic. Researchers detected an increase in stalkerware, software programs, apps and devices that enable someone to spy on you through your device by tracking your movements, reading your text messages, and viewing your phone call history.
Additionally, the 2021 Norton Cyber Safety Insights Report (NCSIR): Special Release – Online Creeping details concerning stalking behaviors and attitudes around the world. Conducted in partnership with the Harris Poll, the study surveyed over 10,000 adults 18+ across 10 countries1.
Two key statistics from the research:
- Nearly one in 10 adults who have been in a romantic relationship (8%) used an app to monitor a current or former romantic partner’s device activity.
- 86% of adults are unaware of stalkerware or have only heard the name.
Here’s the story behind the survey findings and Norton Labs research, including how researchers gathered data on the rise in stalkerware and what you can do to help protect against someone using stalkerware to spy on you.
What’s behind the rise of online stalking?
Technology is a positive tool for many people, but some use it for pernicious purposes.
In fact, 34% of adults globally [1] who have been in a romantic relationship admit to checking in on a significant other online without their knowledge or consent, according to the 2021 Norton Cyber Safety Insights Report (NCSIR): Special Release – Online Creeping.
This behavior, which we’ve coined as “online creeping,” isn’t automatically harmful. For example, when asked why they creeped on their partner online, 38% of those who have, said they were “just curious.”
But some had more charged reasons, including these:
- 40% said they didn't trust their significant other or suspected they were up to no good.
- 39% said they wanted to know where their partner was or who they were with.
- Further, 26% of all adults said online stalking is OK if one or both partners have cheated or are suspected of cheating.
Now, new research from Norton Labs shows that over the past eight months there’s been a dramatic uptick in the number of devices infected with stalkerware, an invasive software often used to spy on the activities of an intimate partner.
Because of lockdowns that have forced many to spend more time at home, personal belongings are easily within arm’s reach, likely creating more opportunities for perpetrators of tech-enabled abuse to install stalkerware on their partner’s devices.
Online creeping behavior turns into cyber stalking when it becomes a compulsive pattern or evolves to include the use of technology and tactics to discreetly track someone’s personal activity or information. Cyber stalking behavior can vary, but it has this in common traits include that: iIt’s unwanted, invasive, obsessive, and often illegal.
How is stalkerware different?
The use of invasive stalkerware apps is one manifestation of malicious cyber stalking.
Stalkerware is best described as software that enables someone to monitor the activities on another person’s device without their knowledge or consent.
When someone installs stalkerware on another’s phone, they can gain access to that person’s personal device activity — such as location, text messages, phone call history, or social media interactions.
While other applications might have some of these capabilities— like location-sharing with friends and family— what differentiates stalkerware is that it’s installed by a third party without the consent or even awareness of the device’s owner.
The classification of an application as stalkerware is not just attributed to its sneaky capabilities, but largely how it is marketed and used.
Stalkerware by the numbers
Stalkerware can take many forms, with the most troublesome conducting surveillance of many of a device’s sensors and communications channels. However, 82% of the apps that can be used for covert surveillance only monitor a single type of device sensor or communication channel.
Which leads to this question: What do stalkerware apps most commonly surveil?
To find out, our Norton Labs team examined thousands of stalkerware apps detected by Norton Mobile Security for Android that appeared on our customer’s devices dating back to August 2020.
Norton Mobile Security for Android has stalkerware detection capabilities, which use a combination of reputation and machine-learning algorithms to flag any apps that can be used for spying. For each app, we used our Norton technology's ability to detect specific stalkerware capabilities to identify the percentage of apps that monitor each of 14 different device sensors and communication channels.
Below, Figure 1 shows the percentage of in-use stalkerware apps that contain each of the features, in blue. However, to give a better sense of the types of surveillance that affect the greatest number of users, Figure 1 also tracks the total number of devices on which the 14 communication channels or sensors are monitored by stalkerware, in orange.
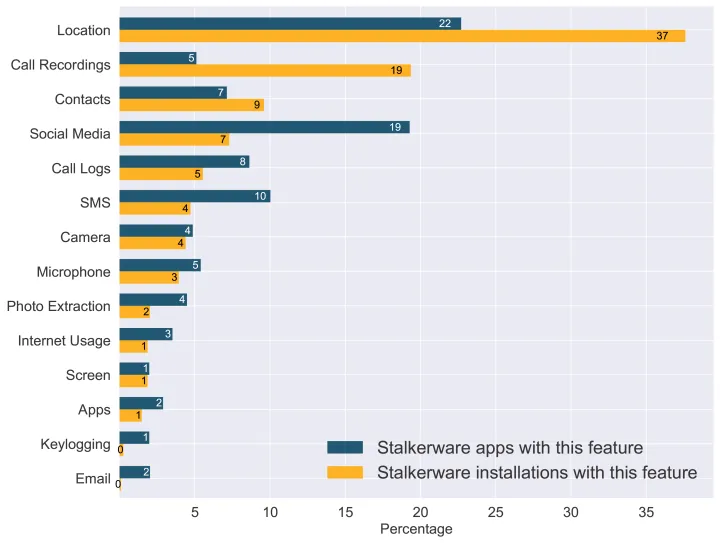
Figure 1: Stalkerware apps may invade the privacy of others through a variety of different means. Here we measure the popularity of stalkerware features that were in use over the 262 days leading up to May 11, 2021 in two ways. First, we measure the percentage of all stalkerware apps that contain each feature. Since some apps with stalkerware capabilities are more popular than others and therefore affect more people, we also measure the percentage of stalkerware installs that contain each feature.
The 14 categories of surveillance, in order of decreasing prevalence by the number of affected users, include:
- Location: The GPS sensor included on most mobile devices enables precise location sharing. Common features of location-sharing apps are minute-by-minute location history tracking overlaid on maps, and geo-fencing alarms that issue an alert when the surveilled device has left an area.
- Call Recordings: Apps that provide automatic call recording functionality are dangerous whether or not the app automatically sends call recordings to another device (many do), because abusive intimate partners typically have easy access to their partner’s device. Many apps focused exclusively on providing call recordings openly advertise themselves as “automatic hidden call recorders.”
- Contacts: Many apps export contact lists from the device. This functionality is typically provided alongside call recording, call log, and/or SMS (text message) monitoring functionality, to enable the stalkerware to tag phone numbers with contact information.
- Social Media: Social media monitoring apps are very common and differ from most other surveillance apps in that they typically perform surveillance from the attacker’s device. By far the most common are WhatsApp surveillance apps based on WhatsApp Web functionality, which requires one-time access to the victim’s device. After this, messages can be monitored remotely from the attacker’s device. Many WhatsApp surveillance apps advertise the ability to read messages without revealing that they have been read, and offer the ability to store messages even if they have been subsequently deleted.
- Call Logs: Many apps offer the capability to collect records of incoming and outgoing phone calls, including call duration and often including contact information as well.
- SMS: SMS, or text message, forwarding and backup applications are commonplace, both for benign and malicious purposes. SMS forwarding is a frequent feature of thorough surveillance apps, though dedicated SMS forwarding apps typically avoid advertising their surveillance potential and instead highlight benign use cases such as guarding against device loss or enabling the convenience of reading SMS messages from a tablet or laptop.
- Camera: Apps that spy on the camera typically also simultaneously enable the microphone. Sometimes these apps advertise as spying apps, but most describe more benign uses, such as turning smartphones into security webcams. In the latter case, the app can typically capture video and audio when the phone appears to be turned off.
- Microphone: Apps that listen in on the device's microphone are likely to also spy on the camera, though this is not always the case. For purposes of this research, we do not categorize apps that have call-recording functionality as microphone-spying apps, though they obviously do make use of the microphone to make call recordings. Also not included in these statistics are a popular class of apps that offer “Super Hearing” spy functionality, because these apps typically are installed on the attacker’s device, and not the victim’s. The attacker might enable the super-hearing app and leave it in a location from which they can eavesdrop on a conversation, while listening in on the device’s microphone from a connected Bluetooth headset.
- Photo Extraction: Many apps offer extraction of photos and other media and files from a victim’s device to a cloud repository. Norton Mobile Security only labels apps this way if the media is extracted in an automated manner that would be undetected by the device owner.
- Internet Usage: Thorough spying apps are likely to collect internet usage data. In doing so, they typically focus on tracking web-browsing history.
- Screen: Screen-recording apps record a video of the user interacting with the device’s screen in a hidden or automated way.
- Apps: Some stalkerware apps collect and report the full list of apps installed on a device, typically in conjunction with usage information or other data.
- Keylogging: Keylogging refers to the collection of text typed into a device through a virtual or physical keyboard. Though rare, apps that provide keylogging capabilities have been proliferating and some have managed to get onto prominent Android app stores. Some apps provide keylogging functionality in conjunction with app enumeration capabilities, so that they can provide reports of messages sent through a variety of different social media apps and email.
- Email: Email is a dangerous communication channel in the hands of an attacker, though perhaps surprisingly, it was the least common communication channel that we saw getting monitored. Unfortunately, abusive intimate partners often gain access to email through other means, primarily through direct knowledge of account passwords.
We found that location tracking, using a device’s GPS sensors, is the most common form of surveillance, both in terms of the number of apps that track location, and the number of users affected by location tracking. However, while many apps are devoted to social media monitoring (with WhatsApp being the most prevalent), hidden automatic call recorders affect more users.
Interestingly, the 2021 NCSIR: Special Release – Online Creeping found that globally [2], more than 1 in 5 adults (21%) say they would be more likely to online stalk if they knew they would not get caught.
Our study also dug into other common cyber stalking behaviors among adults who have been in romantic relationships. The most common stalking behaviors were checking on their partner’s phone to view information like phone calls or emails (16%), reviewing their significant other’s search history on one of their devices (15%), and using knowledge of their partner’s passwords to access their device or online accounts, like social media profiles (12%). One in 10 (10%) also disclosed they tracked their current or former partner’s location via a location sharing app.
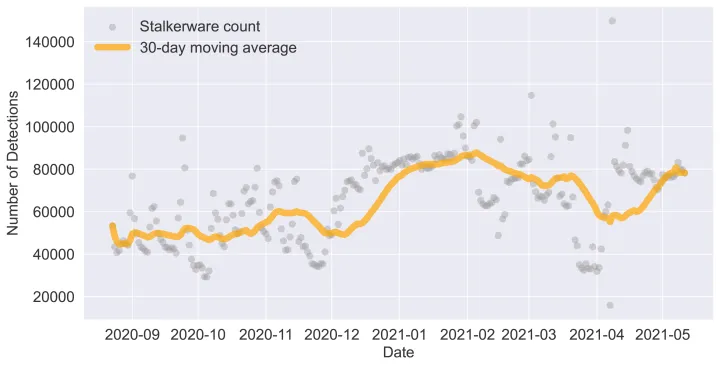
Figure 2: Daily number of Android devices reporting stalkerware over the 262 days leading up to May 11, 2021. Detections climbed by 63% from September 2020 to May 2021.
As the Norton Labs team continued our analysis, we found that the number of devices reporting stalkerware samples on a daily basis increased markedly by 63% between September 2020 and May 2021. Using Norton’s latest stalkerware blacklist, this was recorded with the 30-day moving average rising from 48,000 to 78,000 detections, indicating a rapid growth in only a short amount of time. Overall, 250,000 devices were compromised with more than 6,000 stalkerware variants in the latest month, with many devices infected with multiple stalkerware apps.
How to protect against stalkerware
Alarmingly, despite its rise over the past year, our 2021 NCSIR: Special Release – Online Creeping found a whopping 86% of adults are unfamiliar with stalkerware, 11% are somewhat familiar, and just 4% are very familiar. The discrepancy between stalkerware awareness and use is disconcerting. If stalkerware use is on the rise, yet people don’t know what it is, how can they identify it or know what steps to take if they find it on their device?
Most stalkerware apps are hidden or covert in some way, but many also use cryptic app titles or icons that falsely indicate a benign purpose, such as “Battery Saver” or “System Services.” Prior to Android version 11, apps could hide their app icons from the home screen altogether, making it even harder to know whether stalkerware apps were on your device.
So how do we protect against stalkerware?
The first step is to uninstall any app that you don’t recognize, and if you use an Android, upgrade to Android 11 or a newer version of the Android OS.
In addition, consider what unintended privacy risks the apps on your device may pose. For example, call recorder apps can be configured to record all calls in a transparent manner that another individual could use if they gain access to your phone. Apps that back up media, text messages, and call logs can likewise save your location to a remote location, such as your cloud storage, enabling access to sensitive data for those that have access to your backups. Additionally, anti-theft apps typically enable covert device tracking, and often contain features that enable remote access to the microphone and camera.
Another thing to look out for is parental control apps. These can be useful tools, but many such apps attempt to monitor device behavior in a hidden or secret way without the child’s knowledge or consent. Such apps are problematic, not only because it is best for parents to have open conversations with their children about online safety and the precautions they plan to take, but because any covert parental supervision app can also be used to track the behavior of non-consenting adults.
Overall, it’s best to beware of what functionality you turn on in apps that are mostly benign. For instance, apps like Google Maps offer family and friends tracking feature and lost-device finders like Apple’s “Find My” app, and Android equivalents, enable a device’s location to be tracked. Fortunately, these apps do provide routine notifications and warnings that your device’s location is being tracked, which makes them difficult to use in secret. If location sharing is desired, apps that provide clear notifications are a good choice.
How to take action against stalkerware
If you’re looking to take further steps to protect against stalkerware, it’s always a good idea to install a security app like Norton Mobile Security for Android to monitor your device. This will scan for the presence of potentially unwanted apps and flag them to you so that you can make an informed decision about what’s on your phone. To learn more about Norton Mobile Security, visit https://us.norton.com/mobile-security-for-android.
Stalkerware and cyber stalking are serious Cyber Safety issues. At NortonLifeLock, we work continually to improve our stalkerware detection capabilities and partner with other security vendors through the Coalition Against Stalkerware to share resources and research. As part of our mission to protect and power everyone to live their digital lives safely, we strive to curb tech-enabled abuse. Furthering our efforts, we recently announced a $75,000 grant to the National Network to End Domestic Violence (NNEDV) to support its Technology Safety program, Safety Net, which provides educational resources and trainings on technology misuse. If you or anyone you know is a victim of domestic violence, including tech-enabled abuse, the National Domestic Violence Hotline also provides confidential and anonymous support 24/7 by phone at 1-800-799-7233, and Loveisrespect provides teens and young adults with confidential and anonymous support by phone at 1-866-331-9474.
About the 2021 Norton Cyber Safety Insights Report: Special Release – Online Creeping
The research was conducted online by The Harris Poll on behalf of NortonLifeLock among 10,030 adults (aged 18+) in 10 countries, of which 8,002 have been in a romantic relationship. The survey was conducted February 15-28, 2021 in Australia (n=1,005), France (n=1,000), Germany (n=1,001), India (n=1,000), Italy (n=1,000), Japan (n=1,020), Netherlands (n=1,000), New Zealand (n=1,004), United Kingdom (n=1,000), and United States (n=1,000, including 808 who have been in a romantic relationship). Data are weighted where necessary by age, gender, race/ethnicity, region, education, marital status, internet usage, household size, and household income to bring them in line with their actual proportions in the population. India was weighted to the population of those who are online. Weighted variables varied by country and included one or more of the following: age, gender, race/ethnicity, region, education, marital status, internet usage, household size, household income, size of place, and propensity to be online. A global postweight was applied to ensure equal weight of each country in the global total. Population projection estimates cited are calculated based on adult population (age 18+) figures from the U.S. Census Bureau’s 2021 International Data Base and Pew Research Center 2017 Global Attitudes Survey. No estimates of theoretical sampling error can be calculated.
[1] Australia, France, Germany, India, Italy, Japan, Netherlands, New Zealand, United Kingdom and United States.
[2] Australia, France, Germany, India, Italy, Japan, Netherlands, New Zealand, United Kingdom and United States.
Innovations from Norton Labs are for research, evaluation, and consumer feedback purposes. NortonLifeLock does not give any warranties as to the suitability or usability of these prototypes and recommends safeguarding data and reviewing all terms and conditions before use.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries.